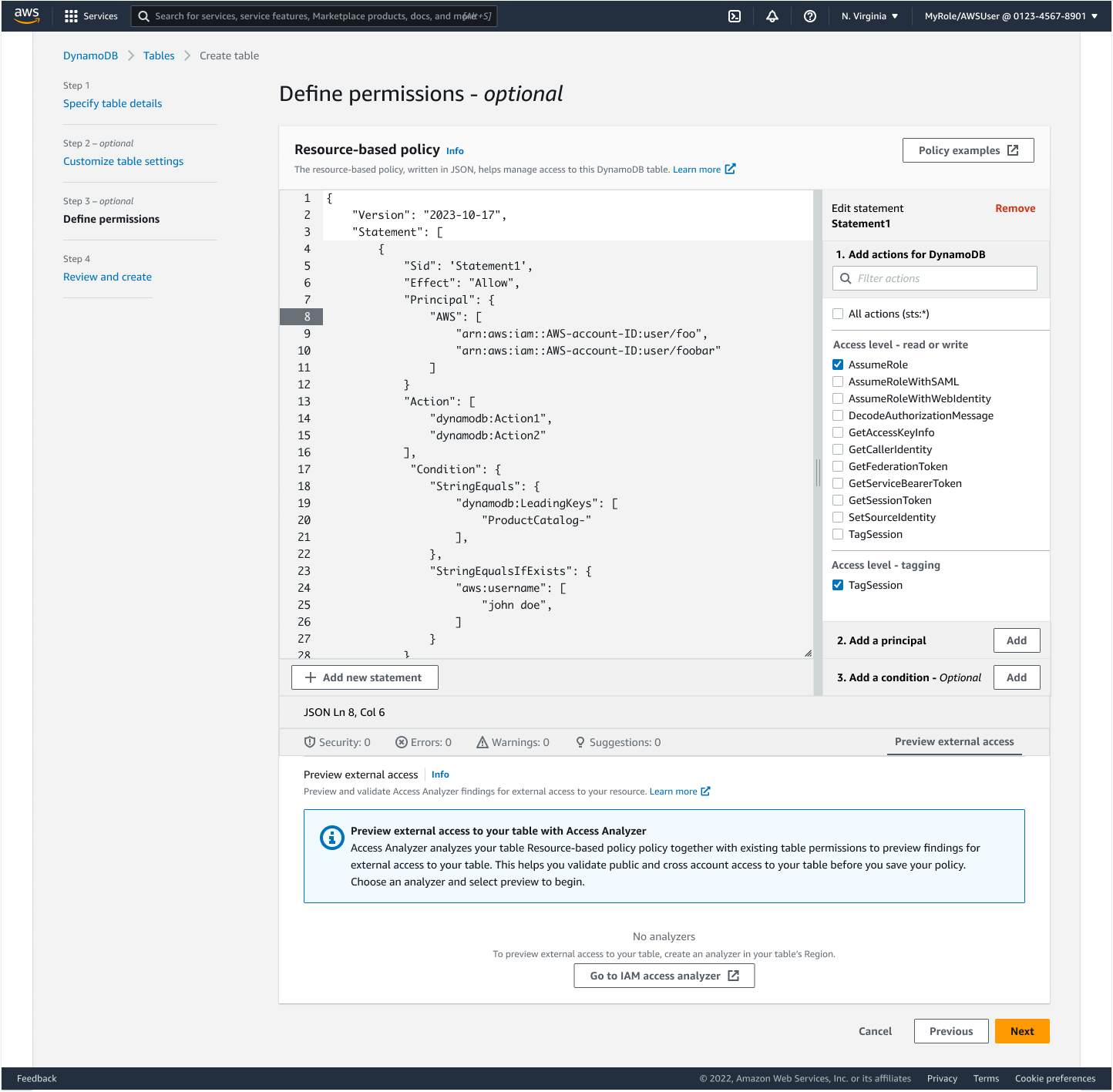
DynamoDB Resource-based Policies
Summary
Led end to end design for DynamoDB's resource-based policies feature that allows customers to manage access permissions directly on DynamoDB tables and streams.
This replaced the previous identity-based policy system and simplified cross-account access management.
Problem
DynamoDB's identity-based access control had three main limitations:
- Permission Management: Access permissions had to be defined in multiple IAM policies across different AWS accounts
- Cross-Account Setup: Required creating IAM roles in both accounts and setting up trust relationships
- Maintenance Overhead: Each new cross-account access required updating multiple IAM policies
This affected large AWS customers including Zoom, JP Morgan Chase, Snap, and Capital One.
Success Metrics
Tracked three key metric categories:
Adoption:
- Policy adoption rates for tables and streams (total count and % per customer)
- Enterprise customer feedback and satisfaction
Task Success:
- Creation success rate for tables with policies
- Success rate of policy additions to existing resources
Usability:
- Drop-off rates in creation/policy flows
Key Design Decisions
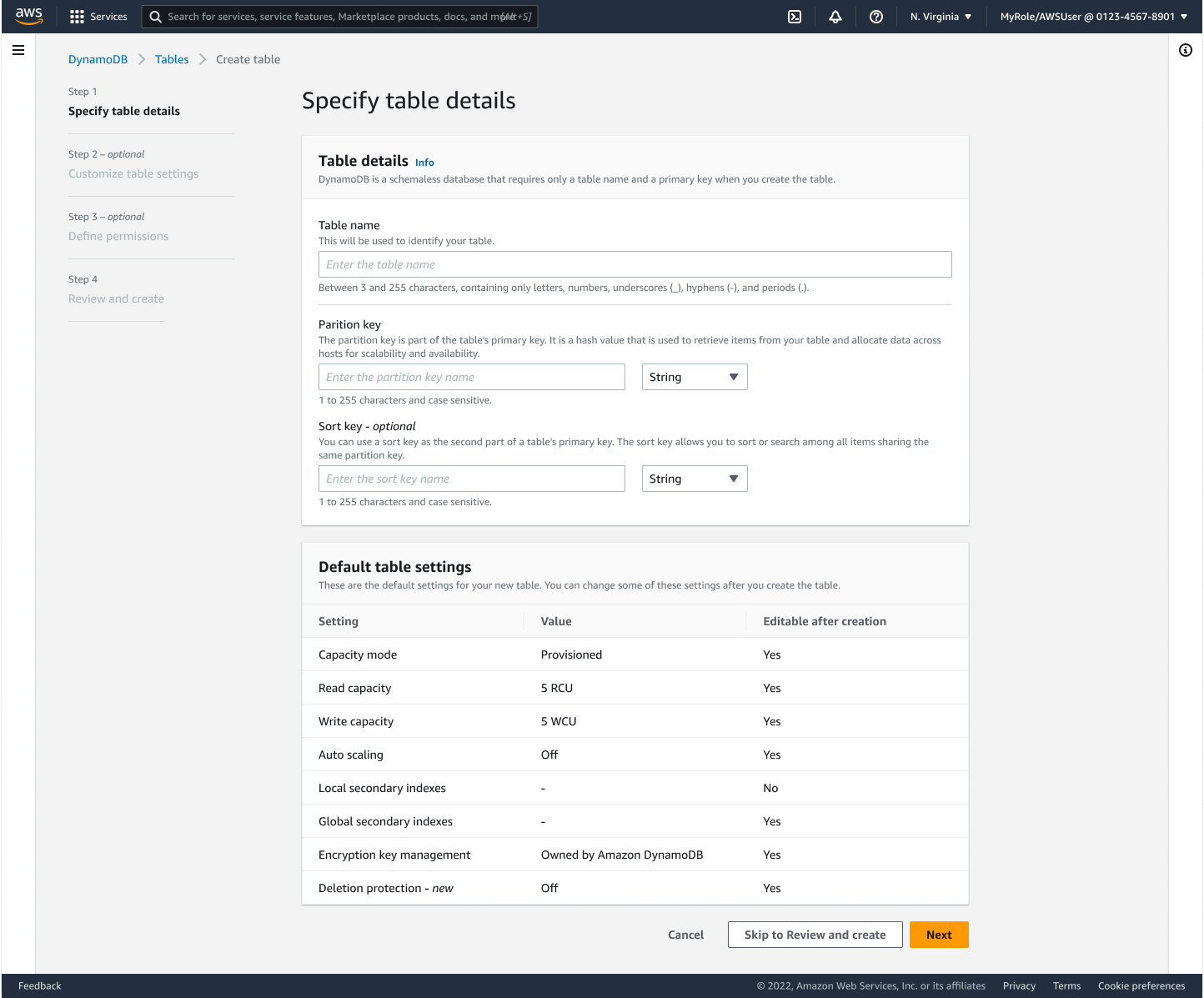
1. Multi-Step Creation Flow
Analysis of 6 months of usage data showed:
- 71.33% of customers created default tables
- 28.67% used advanced configurations
Implementation:
- Four-step creation process: details → settings → permissions → review
- Added quick create option for default tables
- Advanced features like resource policies shown only when needed
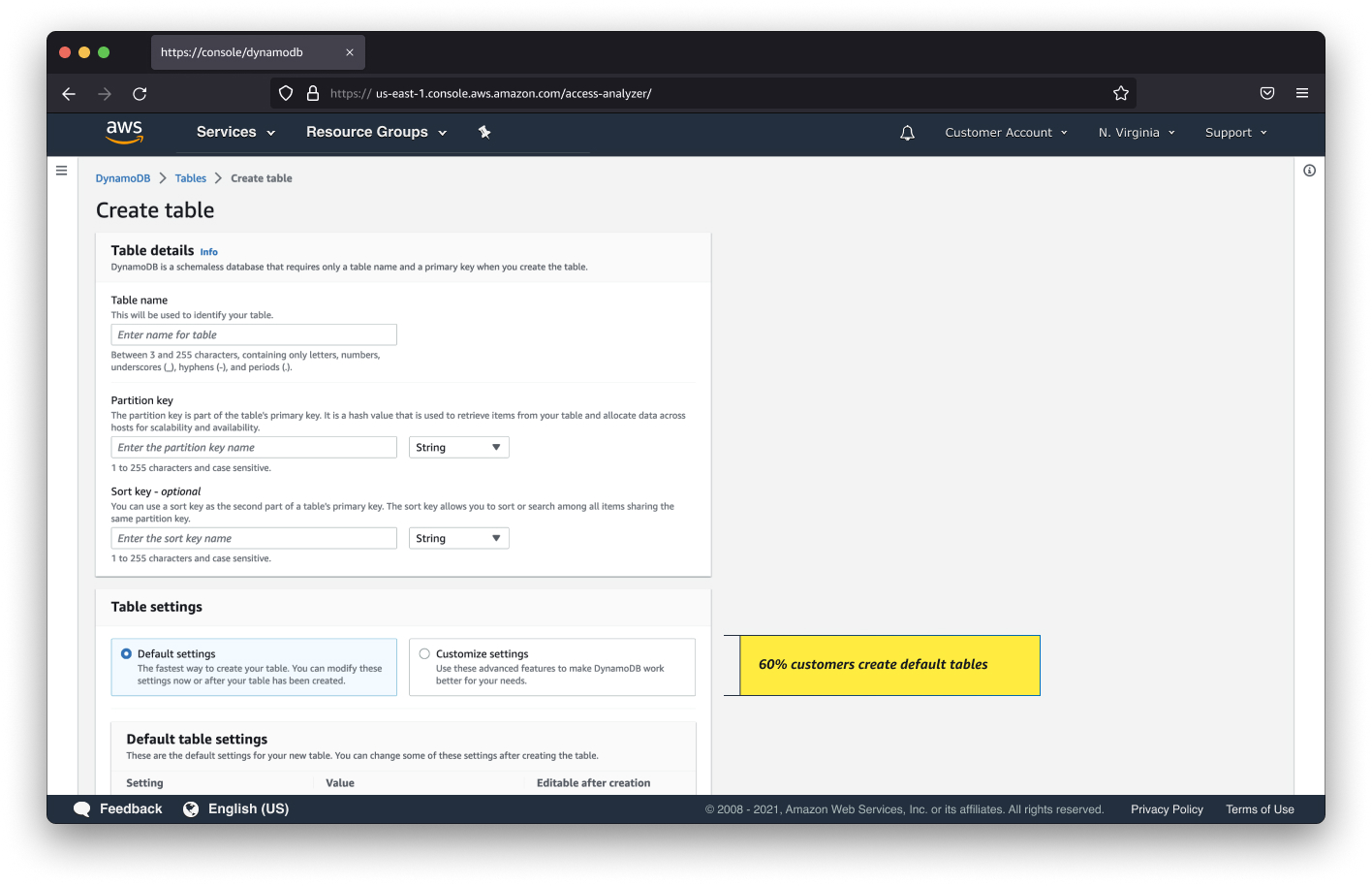
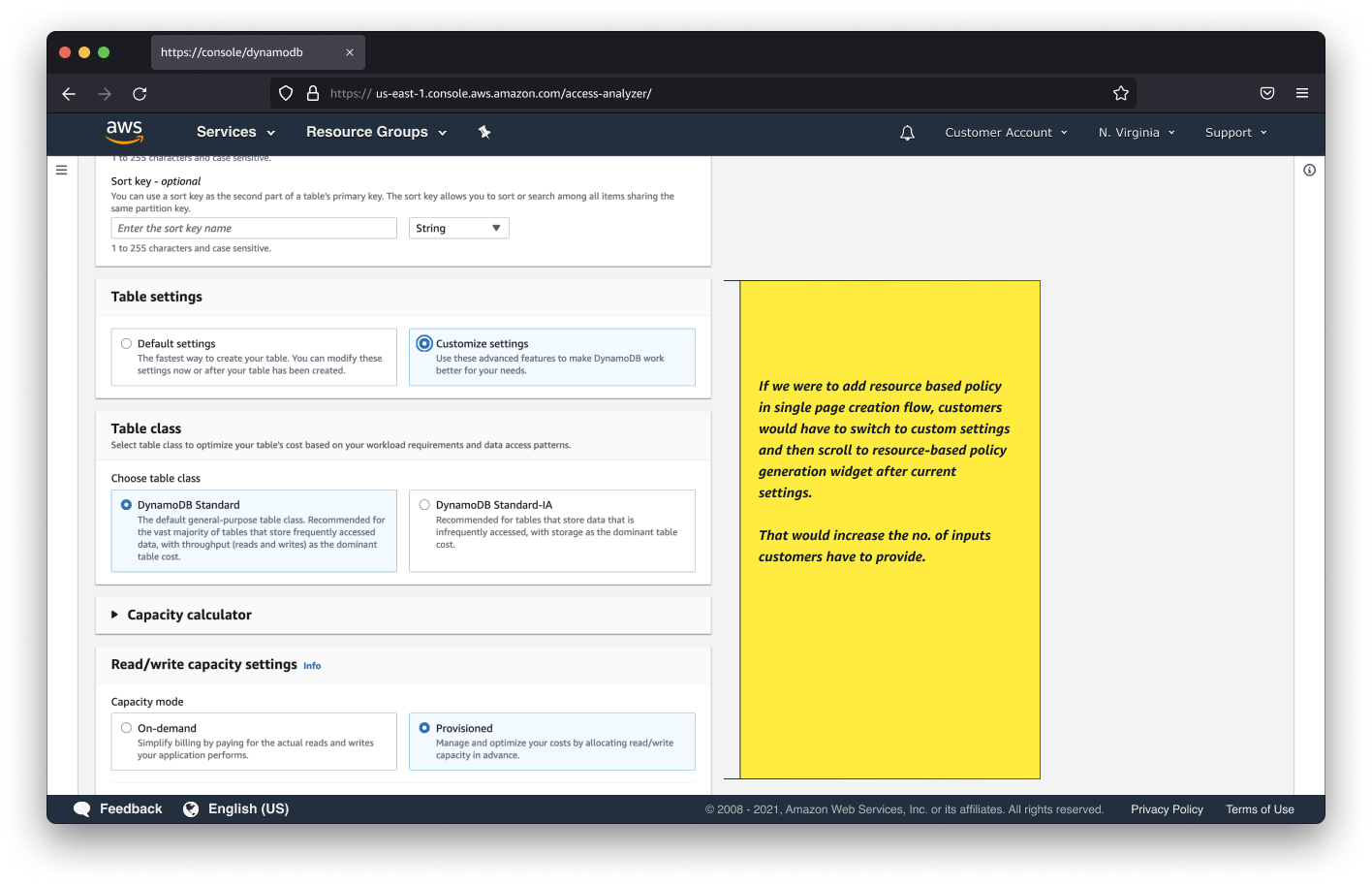
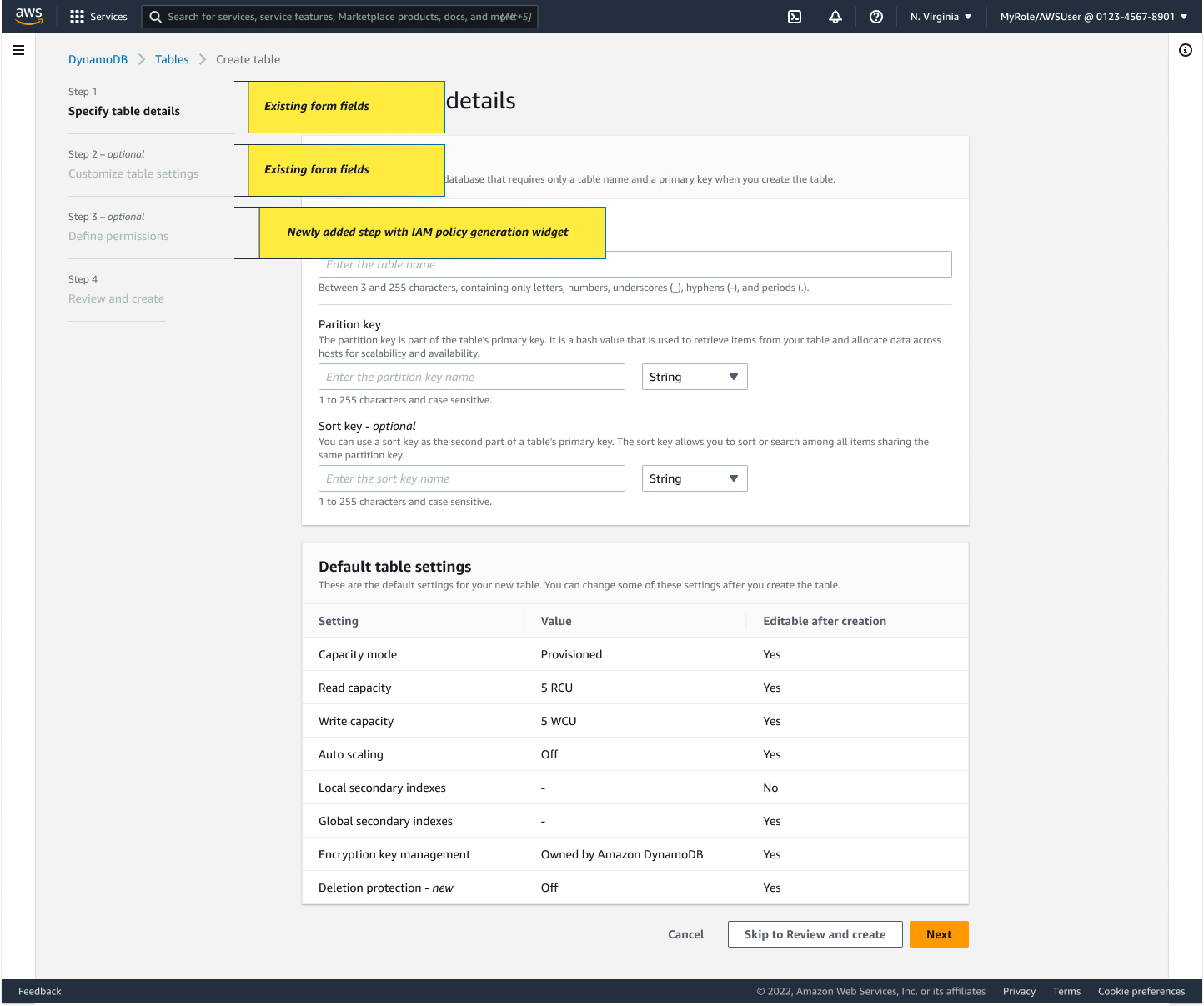
This approach balanced two key user needs:
- Maintaining simplicity for novice users creating default tables
- Supporting advanced users with complex configuration needs
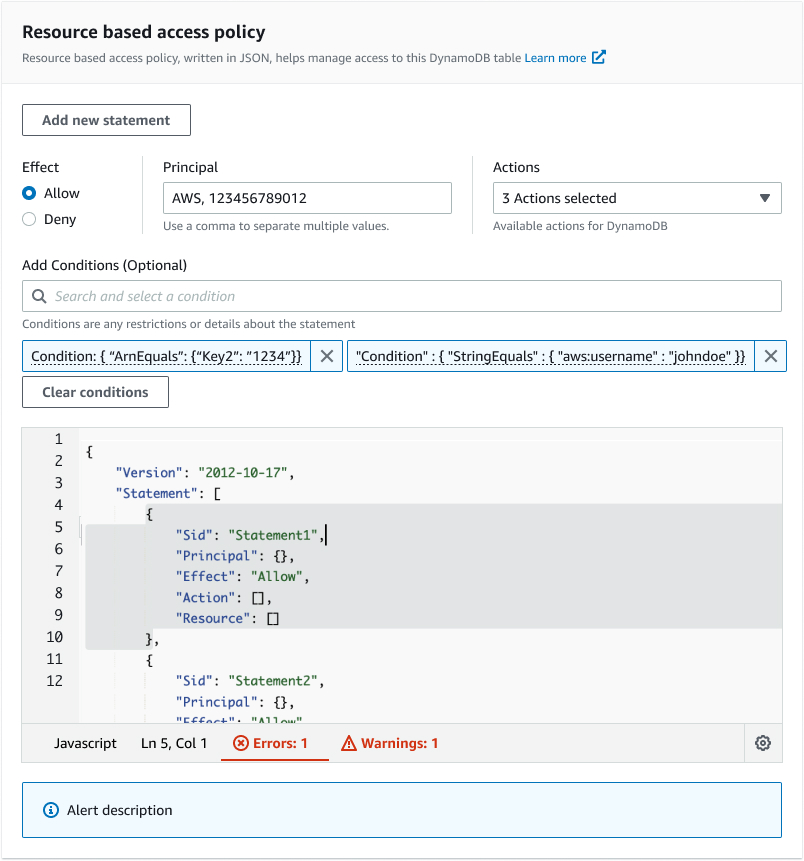
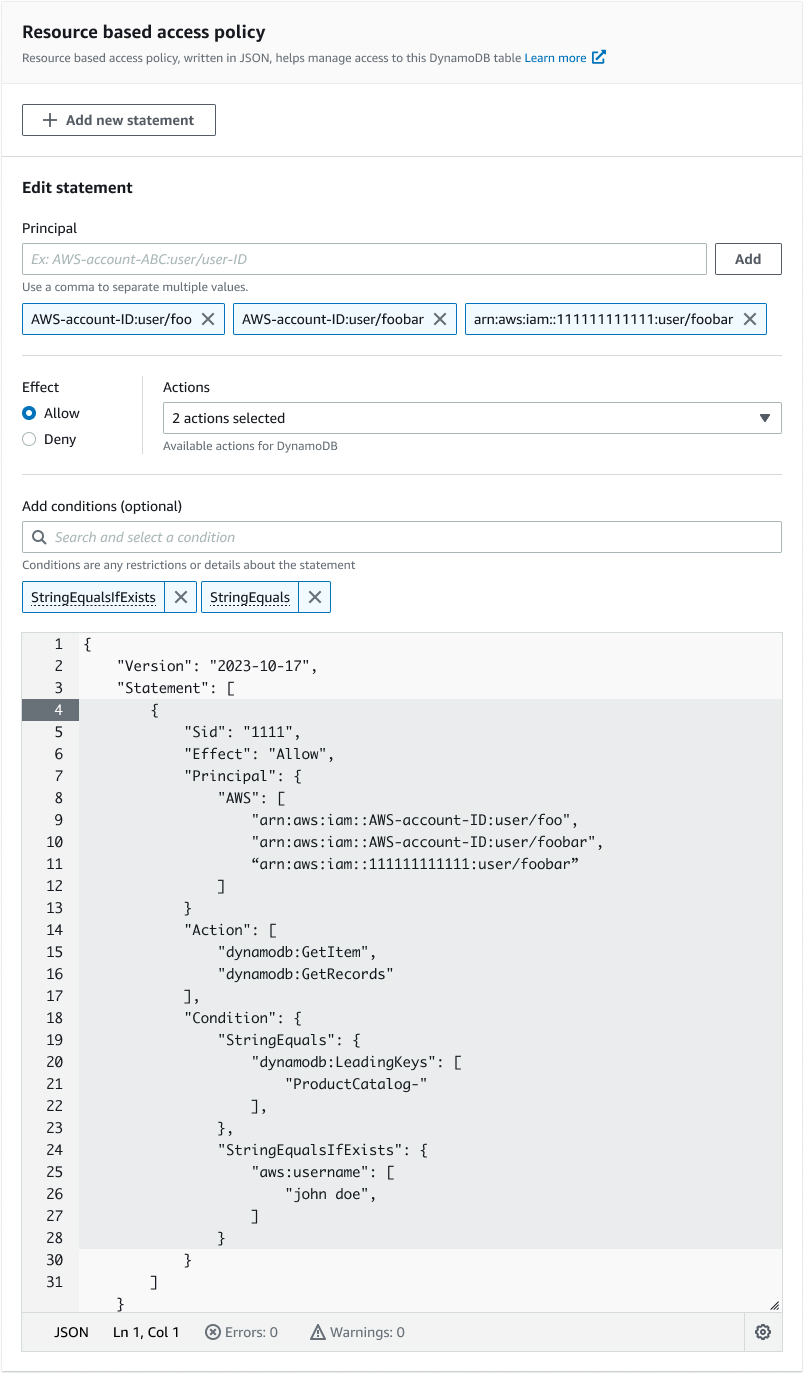
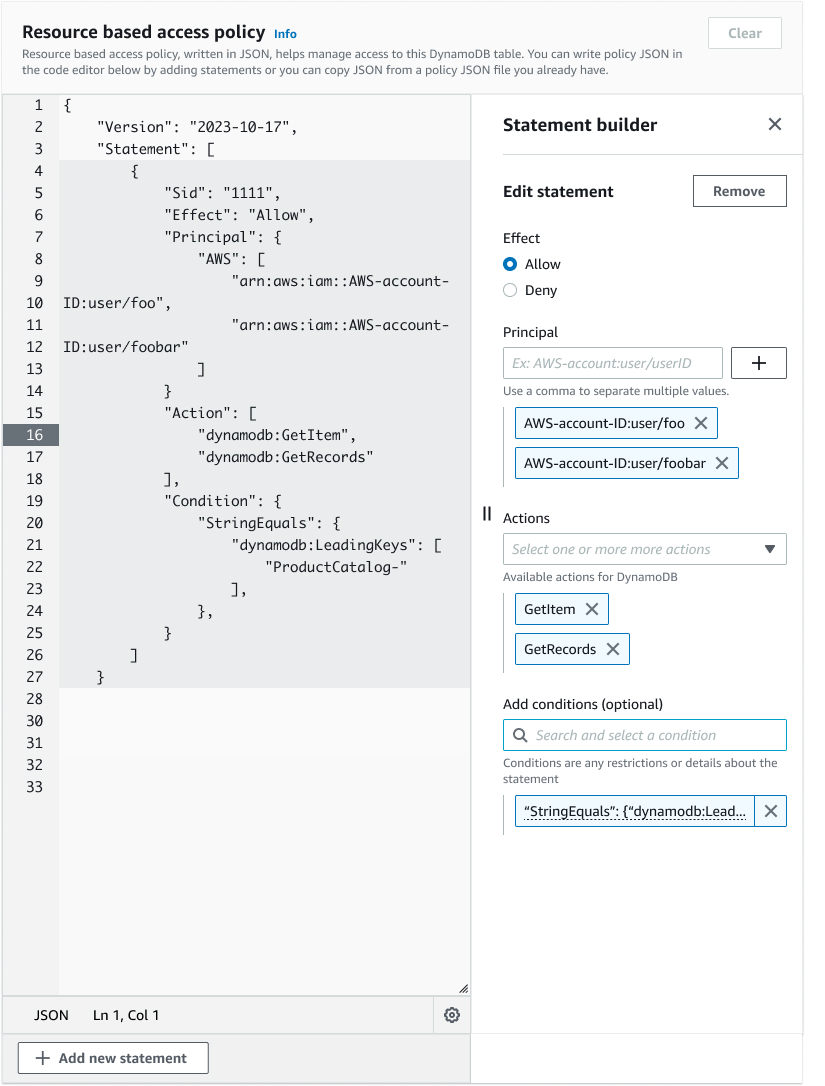
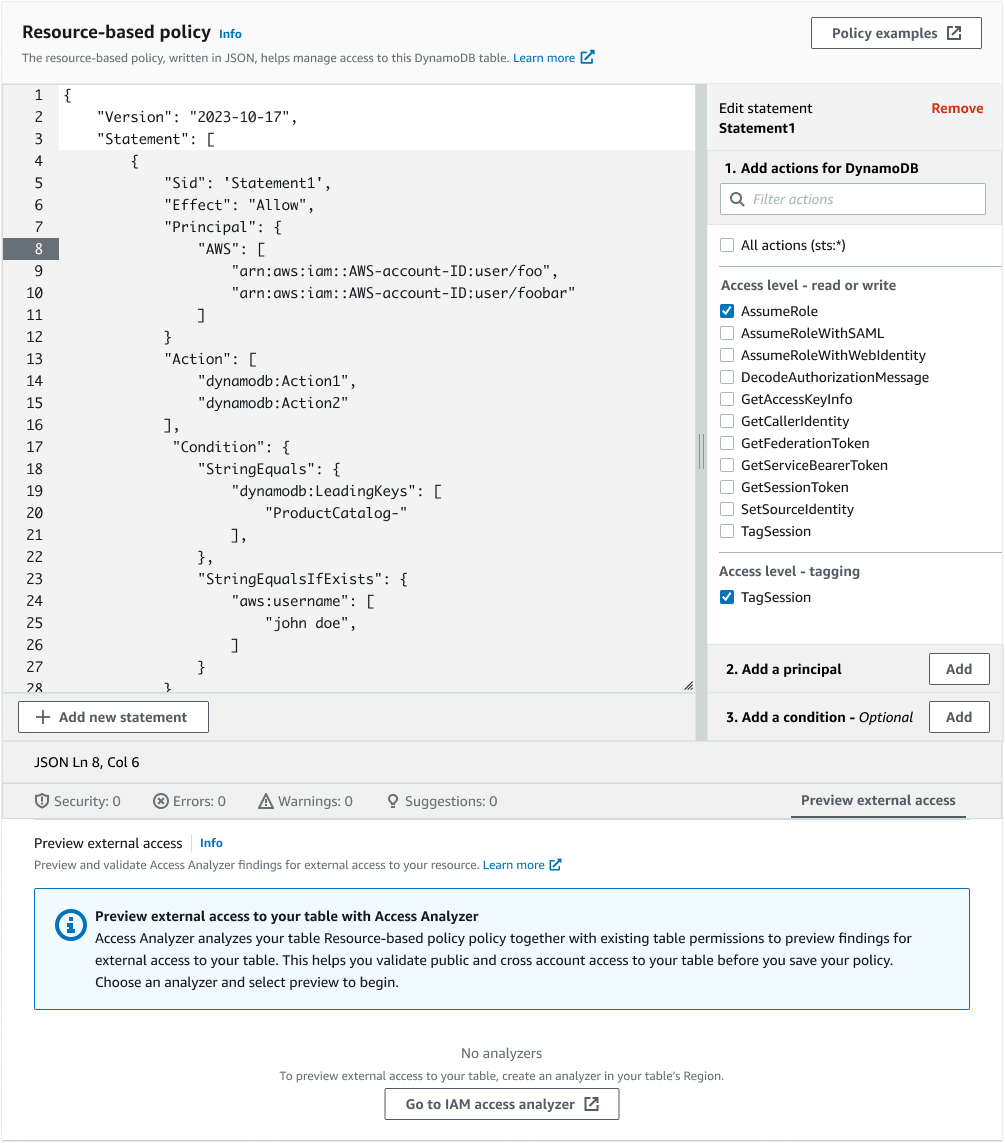
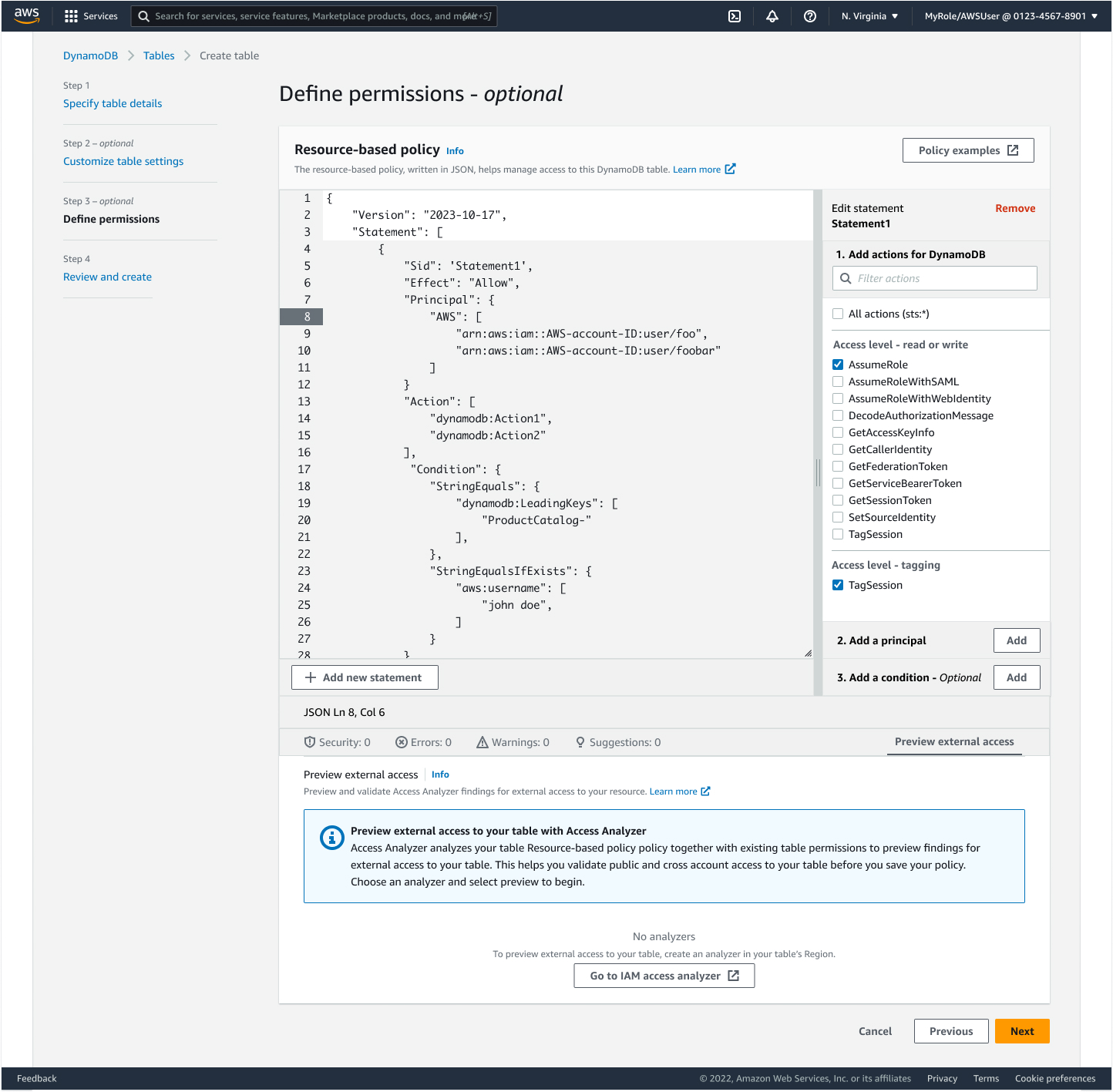
2. Policy Editor Implementation
We faced a critical decision between building an in-house solution versus leveraging existing components:
| Aspect | Built with In-house APIs | Existing IAM Policy widget APIs |
|---|---|---|
| Customization | Custom-built for DynamoDB policy statements | Limited customization options |
| Integration | Direct integration with DynamoDB use cases | Pre-built with IAM access analyzer |
| Development | Required building validation logic from scratch | Production-tested and app-sec approved |
| Design | Full control over UI/UX | Bounded by IAM policy information architecture |
We chose to be frugal and leverage the existing IAM policy APIs to power the policy editor, focusing our efforts on improving the integration points and user experience.
Core Features
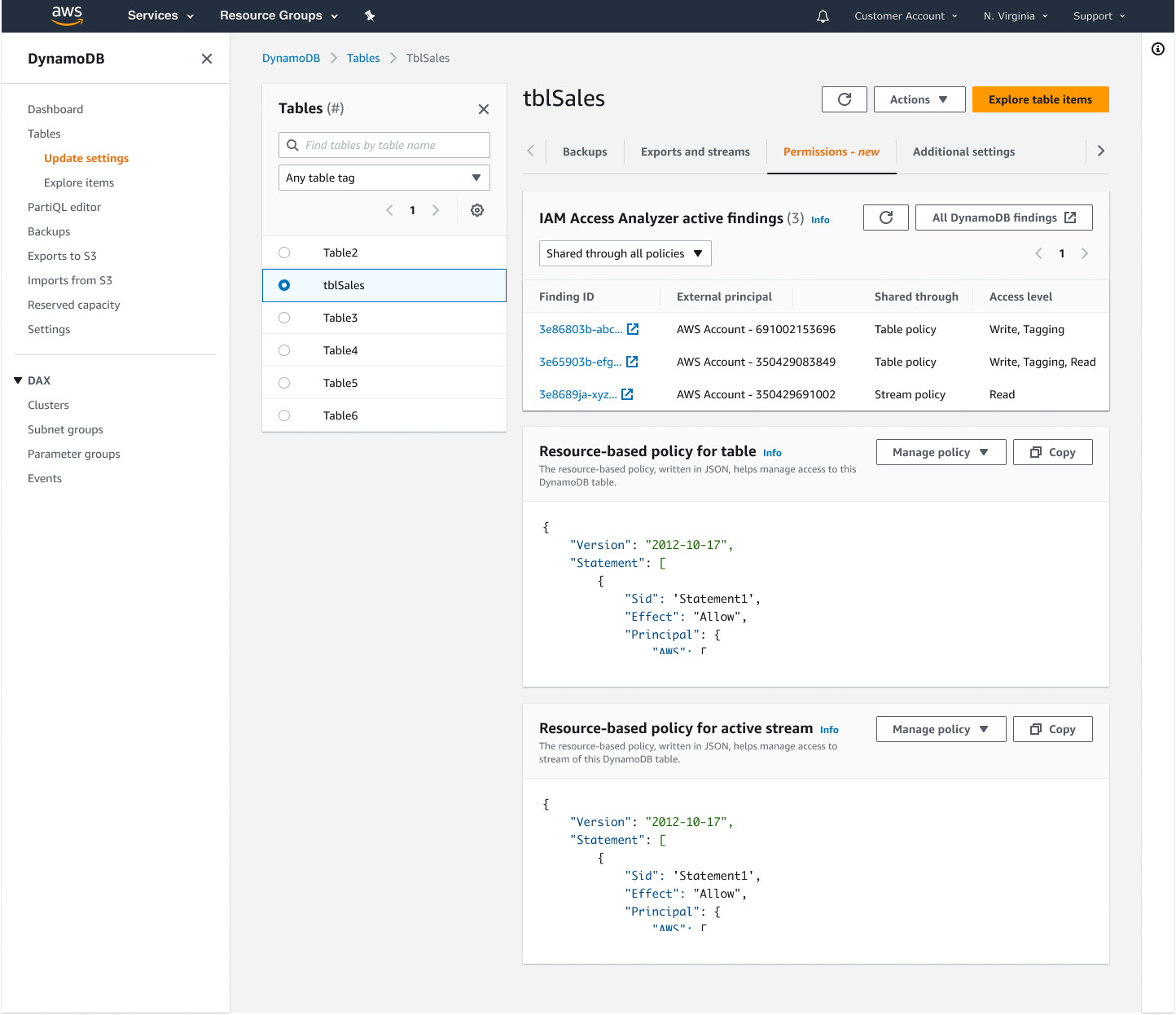
Resource-Centric Authorization
- Centralized permission management at the resource level
- Fine-grained access control for tables and their indexes
- Simplified cross-account access management
Policy Generation Experience
- Integrated IAM Access Analyzer for policy validation
- Resource-pivoted view of access analyzer findings
- Streamlined policy authoring interface
Multi-Page Creation Flow
- Redesigned table creation workflow
- Scalable configuration system for advanced users
- Simplified long-form input patterns
Challenges
Technical Integration
- Enhanced widget capabilities through IAM team collaboration
- Resolved cross-console API limitations for permission detection
Cross-Team Alignment
- Drove IAM Access Analyzer integration and resource-view roadmap
- Coordinated implementation across IAM, Security and Legal teams
- Ensured compliance with AWS security standards through legal review
Impact
-
Technical Improvements:
- Reduced cross-account setup steps from 7 to 2
- Centralized permission management per resource
- Added automated policy validation
-
User Experience:
- Simplified multi-step table creation
- Added guided policy creation
- Improved error handling and validation
Learning
What Worked:
- Using existing IAM components saved 3 months of development
- Early security team involvement prevented rework
Issues Faced:
- Required additional error handling for cross-account scenarios